Blockchain can therefore represent an important step for the digitization of the public sector. In turn, an efficient e-government system would lead to a reduction in economic costs and wasted time. Given the sharing of data, both in intra-governmental relationships and between the public and private individuals, there would be a reduction in the bureaucratic complexity and discretion of public employees. Furthermore, given the greater accessibility to e-government systems, probably via apps or web platforms, the distance between citizens and institutions would be reduced.
For companies, the discussion is similar: having a shared database can help in relations with the State as regards the simplification of formal obligations, and with consumers as regards the management of information databases, their sharing with interested parties, subject to authorization of consumers, and the most precise planning of business activities.
All that glitters is not gold
In the light of these considerations, it is necessary to ask why a technology to which is attributed such a high potential has so far found so limited applications.
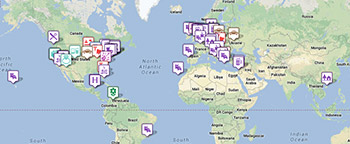
A first problem in the de.bitcoineras.com is that the blockchain, being a complex technological network of computers, consumes a huge amount of electricity. To approve each new operation, the majority of the network nodes, represented by computers, must verify the integrity of the data and the compliance with the blockchain rules, with the so-called "Proof of Work" mechanism. Each computer performs millions of data control and encryption operations, a task that in jargon is called "hashing", which consists in transforming large amounts of information into a single encrypted alphanumeric code, of 160 or 256 bits. The more numerous the subjects that use the blockchain the more complex the hashing system becomes complex, slow and expensive of energy. According to some estimates, the only blockchain system applied to bitcoins, given the expenditure of electricity, entails a CO2 emission equal to the city of Singapore, or more than Sri Lanka, Nigeria and Norway;[6] This result is visible from the map below (Figure 1), which compares the energy consumption for bitcoins with the current one in the various countries in 2018.
The social cost due to pollution therefore represents one of the main limitations of the blockchain.
A second problem is that the decentralized system becomes increasingly complex with the increase of new users therefore the hashing system (encryption) becomes increasingly slow in carrying out the checks for writing the new blocks.
A third problem is that there is a physical limitation due to the ability to manage information. We know that information is never deleted once it is inserted into the blockchain, therefore it is legitimate to wonder how long it will be possible to insert new blocks in the chain, and how many computers will be needed to support the growth of the network, in the event of a massive application of the blockchain . The graph below (Figure 3), which represents the growth in the size of the blockchain, shows that there is an exponential increase in its use, connected to an increase in its size in terms of occupied memory. For example, in 2012 the memory occupied by the blockchain on each node was 216 megabytes, compared to over 265,000 MB in 2020, equivalent to about 265 GB, which each node records inside.
Another limitation of blockchain technology is the threat of the "51% attack". The other networks, other than the blockchain, typically have a centralized HUB, which is necessary to keep the network running and which, in the event of a target attack, would end the entire network (so-called systemic risk). The blockchain, on the other hand, is a decentralized and distributed network; therefore no one can take over a central node and to bring down the network. However, there is a risk, known as "51% attack", which could occur if a person, or an organization, takes control of the majority of the nodes in the chain. This is a fairly remote hypothesis since the network is very extensive and it would still not be possible for hackers to modify all the information previously recorded to appropriate, for example, information and properties from other nodes, considering that these would still be encrypted and accessible only through the owners' private keys.


 Updated every 10 minutes
Updated every 10 minutes